Introduction: When Security Experts Become Attackers
Here's something that hits different: two of the people supposed to be protecting companies from ransomware attacks actually orchestrated them. In October 2024, the Department of Justice indicted three cybersecurity professionals for carrying out ALPHV/Black Cat ransomware attacks that targeted multiple US companies. By late 2024, two of them had already pleaded guilty, and their case reveals something uncomfortable about the cybersecurity industry.
Ryan Goldberg, a 40-year-old incident response manager at Sygnia Cybersecurity Services, and Kevin Martin, a 36-year-old ransomware negotiator at Digital Mint, admitted to using sophisticated hacking tools they learned through their legitimate jobs to extort $1.2 million in Bitcoin from victims. They didn't just attack one company. They went after a medical device manufacturer, pharmaceutical companies, doctor's offices, engineering firms, and even a drone manufacturer. The third conspirator, whose identity hasn't been publicly disclosed, worked alongside them as another ransomware negotiator.
What makes this case particularly significant isn't just that it happened, but what it exposes about insider threats in cybersecurity. These weren't amateur hackers operating from their basement. They were credentialed professionals with years of experience defending against the exact attacks they were now committing. They understood network architecture, knew how to evade detection, understood incident response procedures, and could negotiate with victims because that was literally their day job.
The prosecution represents a growing concern in the industry. As cybersecurity becomes more lucrative and the barrier between defense and offense blurs, we're seeing more cases of insiders weaponizing their knowledge. This isn't a theoretical problem anymore. It's playing out in courtrooms and in the networks of real companies. This article explores what happened, why it matters, and what it means for the future of cybersecurity defense.
TL; DR
- Two cybersecurity insiders pleaded guilty to ALPHV/Black Cat ransomware attacks targeting multiple US companies and extorting $1.2 million in Bitcoin
- Insider threat risk is escalating because security professionals have access to systems, understand defensive measures, and can evade detection
- ALPHV/Black Cat is a major threat actor with a ransomware-as-a-service model responsible for attacks on Reddit, MGM Resorts, United Health, and Bandai Namco
- The attack surface expanded in 2023-2024 as remote work, legacy systems, and cloud migrations created more entry points for insiders
- Organizational response must shift toward behavioral monitoring, privilege access management, and zero-trust architecture

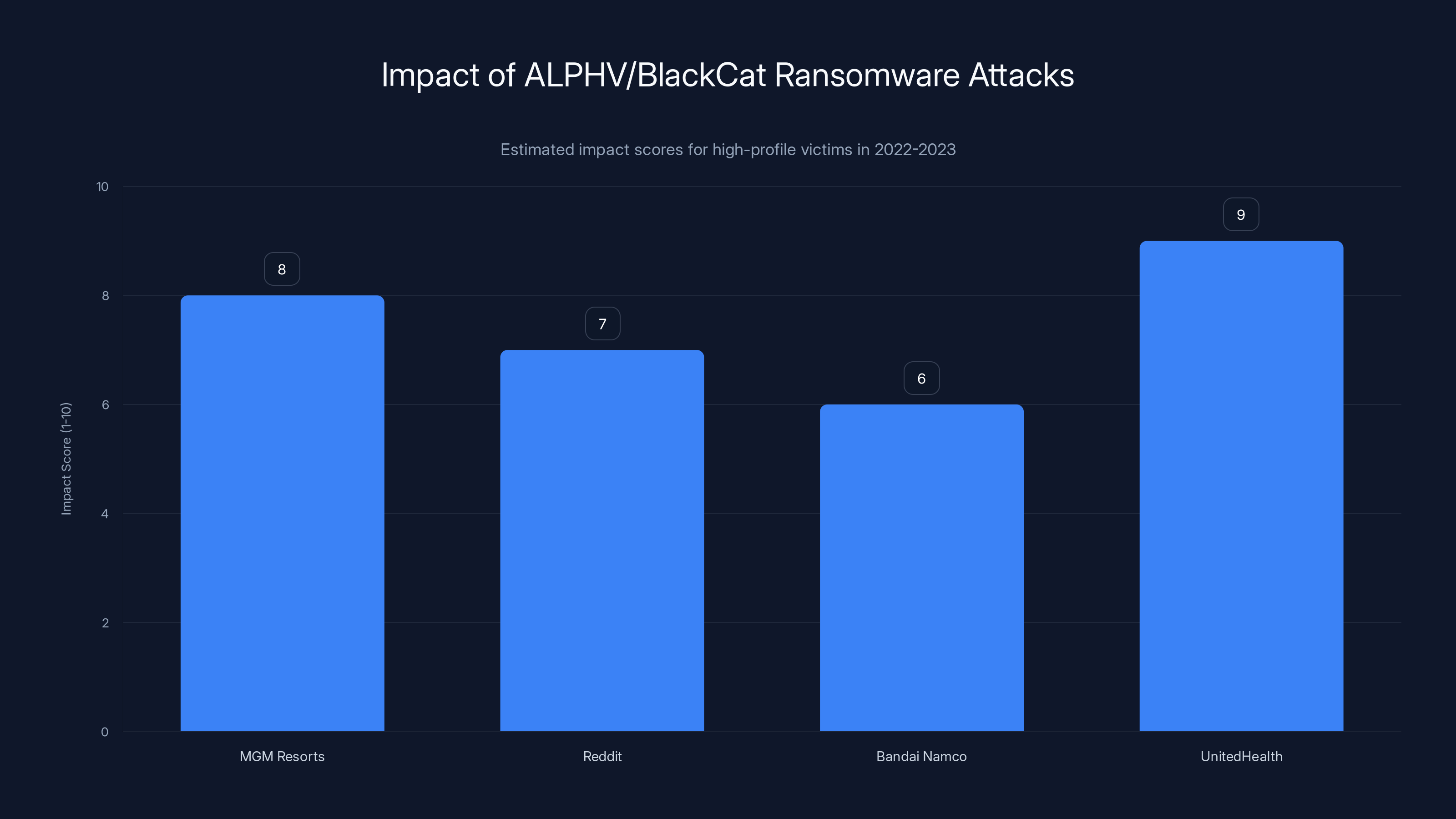
Estimated impact scores indicate UnitedHealth faced the most significant disruption due to ALPHV/BlackCat attacks, followed by MGM Resorts. Estimated data.
The Case: What Actually Happened
The Defendants and Their Roles
Ryan Goldberg held the title of incident response manager at Sygnia Cybersecurity Services. Sygnia isn't a small boutique firm. It's a legitimate, established cybersecurity company that provides incident response and threat intelligence services to enterprises. Goldberg's job involved responding to actual security incidents, understanding attack methodologies, and helping clients recover from breaches.
Kevin Martin and the unnamed third conspirator worked at Digital Mint, another incident response company. Martin specifically held a position as a ransomware negotiator. Think about what that job entails: understanding threat actor tactics, knowing how ransomware groups operate, communicating directly with attackers, and negotiating payment amounts. Martin had a front-row seat to how ransomware attacks work, what demands work, and what doesn't.
These weren't people struggling with basic cybersecurity concepts. They understood incident response procedures, knew how organizations detect intrusions, understood network architecture, and had seen firsthand what mistakes companies make that lead to breaches. They had legitimate access to detailed information about how attacks happen and how defenses fail.
The Timeline: 2023 ALPHV Attacks
In 2023, Goldberg, Martin, and their unnamed co-conspirator deployed ALPHV/Black Cat ransomware against multiple organizations. The Department of Justice's indictment details a coordinated campaign targeting victims across different industries. They weren't haphazardly choosing targets. The victim list suggests a deliberate selection process.
Their first confirmed victim was a medical device manufacturer. Ransomware groups typically research targets before attacking, understanding revenue, insurance coverage, and likely willingness to pay. A medical device company fit the profile perfectly: critical operations they can't afford to lose, likely cyber insurance with high coverage limits, and potential regulatory pressure to pay quickly to restore operations.
Following that success, they expanded to pharmaceutical companies, doctor's offices, engineering firms, and a drone manufacturer. The medical device company attack alone netted them over $1 million in Bitcoin payments. That's not chump change. That's meaningful financial incentive for sophisticated criminals.
How They Did It: Technical Details
The attacks leveraged ALPHV/Black Cat ransomware, which emerged as a prominent ransomware-as-a-service platform around 2021. Black Cat represented a new generation of ransomware built with modern programming languages like Rust, designed to be faster, stealthier, and more effective than earlier variants like Dark Side or REvil.
ALPHV/Black Cat operates on a ransomware-as-a-service model. The developers create and maintain the malware code. They then rent it to affiliates who conduct actual attacks. When an attack succeeds and victims pay ransom, the platform developers take a cut, typically 10-25% of the payment. This model scales the threat exponentially because it lowers the barrier to entry for attackers while distributing revenue among dozens of actors.
Goldberg and Martin used their insider knowledge to accelerate the attack process. They understood incident response timelines, knew what alerts organizations monitored for, and could likely identify gaps in detection systems. They knew how companies respond to infections because they'd responded to infections themselves. This knowledge compressed the typical attack timeline significantly.
The Bitcoin Trail and Extortion
The conspirators demanded and received $1.2 million in Bitcoin across multiple victims. That figure represents the confirmed amount prosecutors could trace. The actual amount could be higher, especially given the difficulty of tracking Bitcoin across multiple wallets and exchanges.
Ransomware payments have been a growing source of concern for law enforcement. In 2023, ransomware payments reached approximately $3.5 billion globally according to law enforcement estimates. Bitcoin's pseudonymous nature makes it attractive for criminals, though blockchain analysis has become increasingly sophisticated.
The extortion process itself highlights another dimension of insider threat. Martin's experience as a ransomware negotiator made him effective at the extortion side of attacks. He understood what threats would be credible, what payment schedules seemed reasonable, and how to communicate pressure without triggering immediate law enforcement involvement. He'd negotiated on behalf of victims before. Now he was doing it from the criminal side.
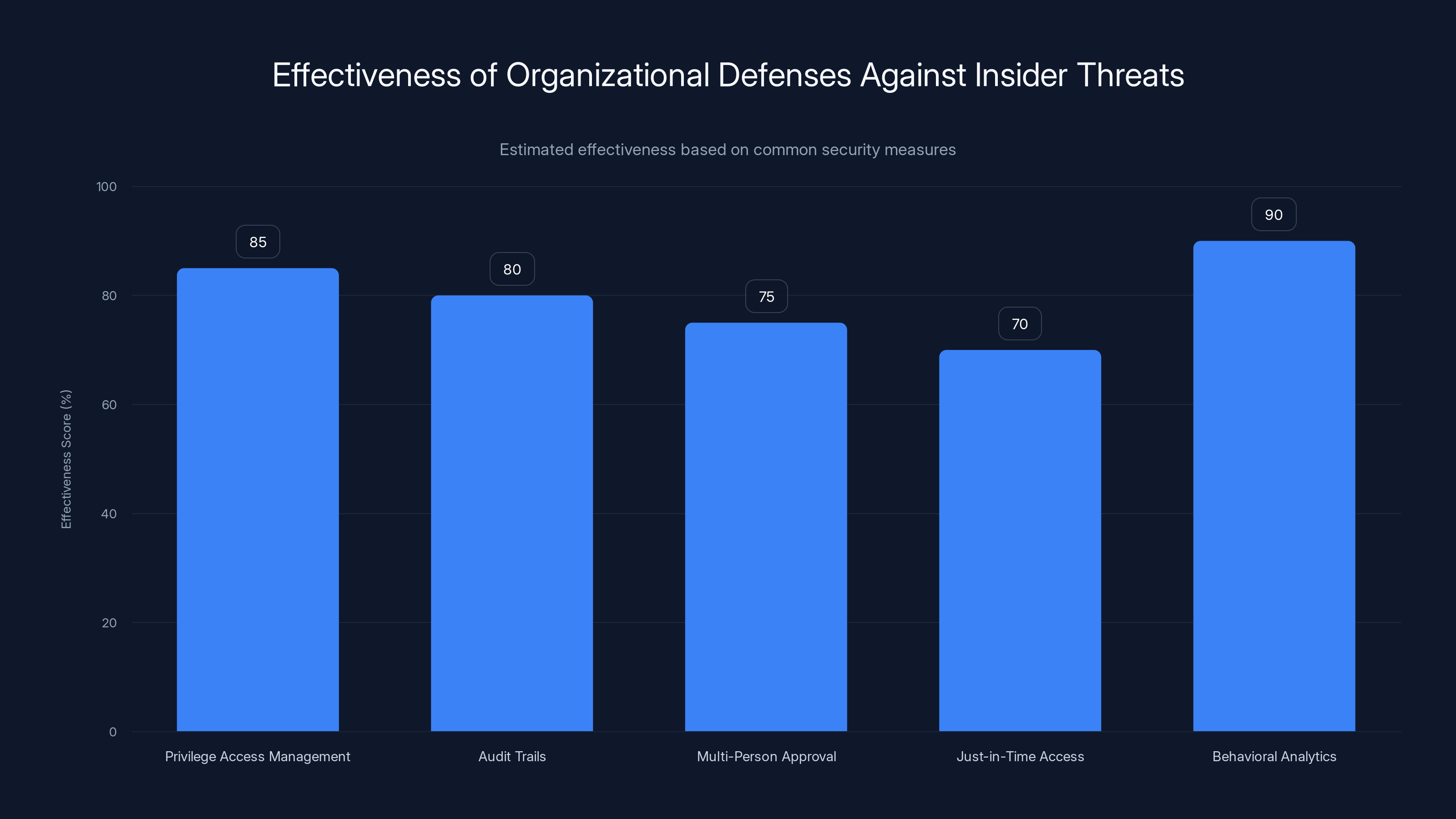
Behavioral analytics is estimated to be the most effective defense against insider threats, with a score of 90%, followed by Privilege Access Management at 85%. Estimated data based on typical security measure effectiveness.
ALPHV/Black Cat: The Ransomware Platform Behind the Attacks
What Is ALPHV/Black Cat?
ALPHV and Black Cat refer to the same ransomware operation, with Black Cat being the more recent operational name. The group emerged in 2021 as a successor to the REvil ransomware platform after law enforcement pressure forced REvil offline. ALPHV/Black Cat learned from REvil's mistakes, incorporating advanced techniques and building a more robust operational infrastructure.
The platform distinguishes itself through technical sophistication. Unlike many ransomware variants written in C++, ALPHV/Black Cat uses Rust, a systems programming language known for speed and efficiency. Rust allows the ransomware to execute faster, encrypt larger datasets more quickly, and run on multiple operating systems with minimal code modification. This architectural choice means the same malware can target Windows, Linux, and mac OS systems effectively.
The ransomware-as-a-service model ensures continued development. As defenses improve and detection methods evolve, the developers actively modify the malware to maintain effectiveness. Affiliates provide feedback on what works and what doesn't, driving constant optimization. This creates a cat-and-mouse dynamic where defenders always lag behind attacker capabilities.
High-Profile Victims and Impact
ALPHV/Black Cat gained notoriety through attacks on major enterprises. In 2022 and 2023, the platform hit companies including MGM Resorts, Reddit, Bandai Namco Entertainment, and United Health Group. The United Health attack was particularly significant, affecting one of the largest healthcare insurance companies and disrupting services nationwide.
The MGM Resorts attack in September 2023 temporarily disrupted casino operations across multiple properties. The group published announcements claiming to have stolen terabytes of data, including customer information and internal systems documentation. The attack highlighted how even well-resourced companies with dedicated security teams struggle against sophisticated threat actors.
Reddit's attack in February 2024 involved exposure of internal documents and code. The group leveraged the attack for not just ransom demands but also to pressure Reddit into changing its API pricing policies affecting third-party applications. This demonstrates how ransomware attacks have evolved beyond pure financial extortion into pressure campaigns targeting company strategy.
Bandai Namco's incident exposed sensitive employee and business information. The video game publisher confirmed the breach but resisted paying ransom, instead working with law enforcement and incident responders to recover systems. This approach became increasingly common as organizations realized that paying ransom doesn't guarantee data deletion and often encourages future attacks.
The Ransomware-as-a-Service Economics
The Raa S model fundamentally changed ransomware economics. Before Raa S emerged, ransomware campaigns typically involved teams of 10-20 skilled operators working directly on attacks. Raa S platforms eliminated this overhead. A developer maintains the malware. Dozens of affiliates conduct attacks. Each successful attack generates revenue that gets split between developers and affiliate operators.
This model scales infinitely. Adding more affiliates doesn't increase costs for platform operators. Each affiliate incentive aligns with platform success. Sophisticated affiliates might negotiate better rates (taking 70% instead of 60%) in exchange for targeting high-value victims. Less sophisticated affiliates might accept lower percentages for easier targets.
The economics explains why ALPHV/Black Cat remains so active despite law enforcement attention. Even with significant law enforcement pressure and successful disruptions, the financial incentives for participation remain enormous. An affiliate hitting a single major victim can earn
Why Insider Threats Matter: The Trust Problem
The Access Advantage
Outside attackers conducting ransomware campaigns follow a predictable sequence. First, reconnaissance gathering information about target systems, identifying entry points, and understanding network architecture. Second, initial access often through phishing, exposed credentials, or public vulnerabilities. Third, lateral movement throughout the network to find valuable systems. Fourth, malware deployment and execution. Fifth, ransom demand and negotiation.
Insider threats compress this timeline dramatically. Goldberg and Martin already had network access. They understood the technical architecture because they'd worked in incident response on those exact types of networks. They didn't need phishing emails or credential theft. They didn't need to move laterally because they were already in trusted positions.
The reconnaissance phase took days for external attackers. For insiders, it took none. They'd already seen what systems were important because they'd responded to incidents affecting those systems. They understood backup strategies, recovery procedures, and incident response timelines because they'd participated in those processes.
This access advantage transforms the threat equation. External attackers might compromise 30-40% of targeted systems. Insider attackers with legitimate credentials might compromise 80-90% of target networks because they can operate more openly, understand what systems to target, and know which detection mechanisms to avoid.
The Detection Problem
Security monitoring focuses on anomalous activity. Unusual login patterns, unexpected file transfers, suspicious processes starting at odd times. All of these detection mechanisms assume that legitimate activity looks normal and attack activity looks abnormal.
But insider attackers already have legitimate activity profiles. Goldberg, as an incident response manager, would reasonably log into various systems, transfer large files, and execute tools and commands. A security analyst reviewing logs might see him launching encoding processes, extracting data, or compiling executables and think nothing of it. His activity falls within the normal range of incident response work.
This creates a fundamental detection problem. The behaviors that legitimate incident responders exhibit—accessing sensitive systems, moving large files, running external tools—closely overlap with insider attack behaviors. Distinguishing between legitimate incident response and malicious activity becomes exponentially harder.
Martin's situation exemplifies this further. As a ransomware negotiator, he regularly communicated with threat actors, understood their tools and techniques, and worked with detailed information about breached systems. An insider communicating externally with potential accomplices would appear to be doing legitimate work.
The Knowledge Problem
Incident response professionals understand security controls, monitoring capabilities, and detection mechanisms in ways that external attackers never can. They see how organizations configure their monitoring systems, what thresholds trigger alerts, and what activities slip through unnoticed.
They understand that security teams often focus on external threats and overlook internal misuse. They know which vendors get monitored closely and which receive less scrutiny. They understand the organizational priority of keeping systems running, sometimes overriding security concerns.
They recognize windows of opportunity. They know that during actual incident response, security controls might be modified or disabled to facilitate investigation. They understand that during systems migrations or upgrades, detection capabilities might be temporarily reduced. They can time attacks to coincide with these windows.
Goldberg and Martin weaponized specialized knowledge that took years to accumulate. They understood not just how to attack systems, but how to attack them in ways that would evade the specific detection mechanisms their employers had implemented.
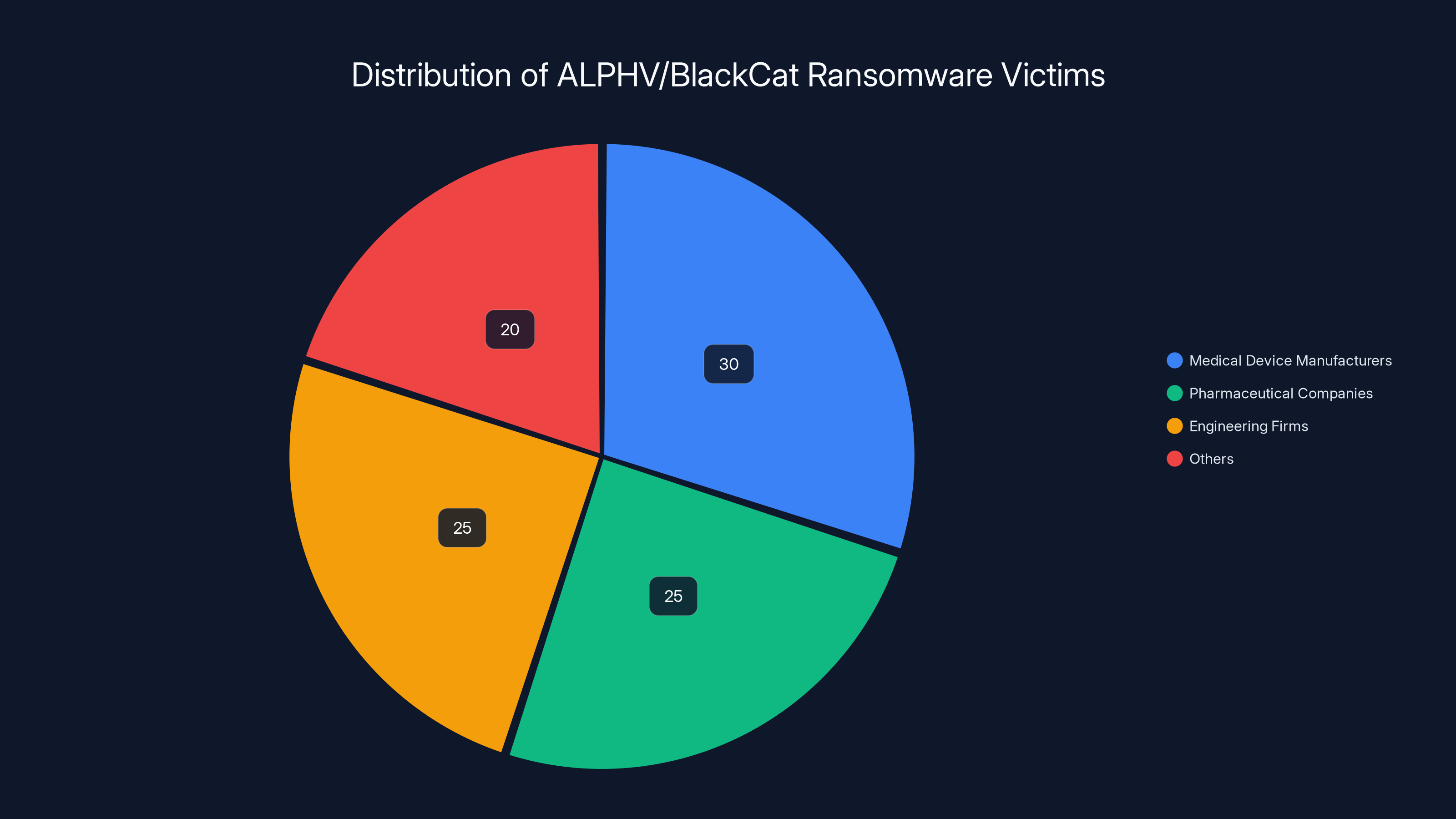
The pie chart illustrates the estimated distribution of ALPHV/BlackCat ransomware victims, highlighting that medical device manufacturers were the most targeted, followed closely by pharmaceutical and engineering firms. Estimated data.
The Legal Consequences and Prosecution
The Charges and Guilty Pleas
The Department of Justice brought charges under conspiracy statutes and extortion laws. Specifically, Goldberg and Martin pleaded guilty to conspiracy to obstruct, delay, or affect commerce or the movement of any article of commodity in commerce by extortion. This legal framing emphasizes the economic damage and the method of pressure applied.
The conspiracy charge itself carries significant weight because it doesn't require prosecutors to prove each defendant personally executed each attack. It only requires proving they agreed to the conspiracy and took at least one action in furtherance of it. This makes the conspiracy charge stick even when specific technical details are murky or when conspirators split responsibilities.
Their guilty pleas represent significant admissions. By accepting guilt, they acknowledge participation in a coordinated campaign to extort money through ransomware attacks. These aren't plea agreements where prosecutors drop charges in exchange for cooperation. These are guilty pleas on the substantive charges themselves.
Sentencing and Prison Time
Goldberg and Martin face potential sentences of up to 20 years in federal prison. Their sentencing is scheduled for March 12, 2026, giving their defense teams time to prepare arguments for mitigation. The actual sentence will likely be lower than the maximum, but federal sentencing guidelines offer limited discretion for prosecutors in extortion and organized crime cases.
The potential for significant prison time reflects how seriously federal prosecutors treat insider threats combined with extortion. The prosecutors aren't just punishing ransomware activity. They're punishing the betrayal of trust inherent in an insider attack. An employee with legitimate access who weaponizes that access receives harsher treatment than an external attacker with equivalent technical skills.
Whether Goldberg and Martin cooperate with prosecutors regarding other ALPHV/Black Cat operations or additional conspirators remains unclear. Cooperation agreements could impact sentencing significantly, potentially reducing prison time substantially if they provide valuable intelligence about the broader attack infrastructure.
The Broader Law Enforcement Picture
The DOJ's successful prosecution reflects increased focus on ransomware operators and their affiliate networks. Following the Colonial Pipeline attack in 2021, which disrupted fuel supplies along the US East Coast, federal law enforcement established ransomware task forces with significant resources.
The FBI, Department of Justice, Secret Service, and multiple other agencies coordinated to develop threat intelligence on major ransomware operators. This intelligence sharing improved detection of ransomware campaigns and enabled identification of affiliates like Goldberg and Martin.
International law enforcement cooperation also played a role. While ALPHV/Black Cat appears to be primarily Russian-speaking, the organization has an international affiliate network. Coordinating across borders to identify and prosecute these actors requires sustained diplomatic and law enforcement partnerships.
The prosecution sends a message to other potential insider threat actors. The message is clear: using insider access to facilitate ransomware attacks triggers serious federal charges with potentially decades of prison time. While it won't deter all future insider threats, it establishes consequences that at least some potential actors will consider.
Incident Response Industry Implications
The Trust Model Under Pressure
Incident response firms depend entirely on trust. Clients grant responders access to their most critical systems, sensitive data, and confidential information because they need help during security emergencies. That trust assumption is fundamental to the industry model.
Goldberg and Martin's case undermines this trust model. Clients now face uncomfortable questions: Can I trust incident responders? Are the people I'm hiring to help me actually planning to attack me? How do I verify that security professionals are actually acting in my interest?
This isn't paranoia. It's rational trust calibration based on demonstrated risk. An incident responder with access to your systems could theoretically compromise them during or after the incident response engagement. The technical knowledge and system access are there. The temptation, depending on financial circumstances, might be there too.
Security firms will likely respond by increasing background checks, implementing more robust verification processes, and developing better compartmentalization of access. But these responses only go so far. At some point, you have to trust the people you hire. Complete elimination of trust would make incident response impossible.
The Rise of Background Verification
Major incident response firms will likely implement more extensive background verification for personnel with privileged access. This includes not just criminal history checks and verification of claimed credentials, but also monitoring of financial situations, associations, and online activity.
Some firms may implement periodic polygraph testing for high-access employees, similar to practices in national security clearance work. Others might use behavioral analytics to identify patterns suggesting potential insider threat activity. Still others might reduce the scope of access any single employee has, requiring multiple people to coordinate to compromise systems.
These measures increase overhead and complexity. They also create potential legal risks around privacy and discrimination. An employee with access to sensitive information doesn't expect their employer to monitor their financial situation or social media activity. But after incidents like this, firms may feel obligated to implement these controls to protect clients.
The Talent Problem
Hiring and retaining quality incident responders becomes more difficult when firms must implement intensive monitoring and reduced access controls. The best security talent often has entrepreneurial inclinations and might resent being treated as security risks themselves.
This creates a talent retention problem. Firms need experienced responders with deep technical skills. But those responders can see that working in incident response now involves being subject to intense monitoring and skepticism. Top talent might instead join software companies, hardware manufacturers, or other firms offering better compensation without the associated suspicion.
The industry might actually lose experienced talent to this dynamic. Goldberg and Martin's case serves as a constant reminder to employees in incident response that working in the field involves accepting scrutiny. That scrutiny might push some talent away.
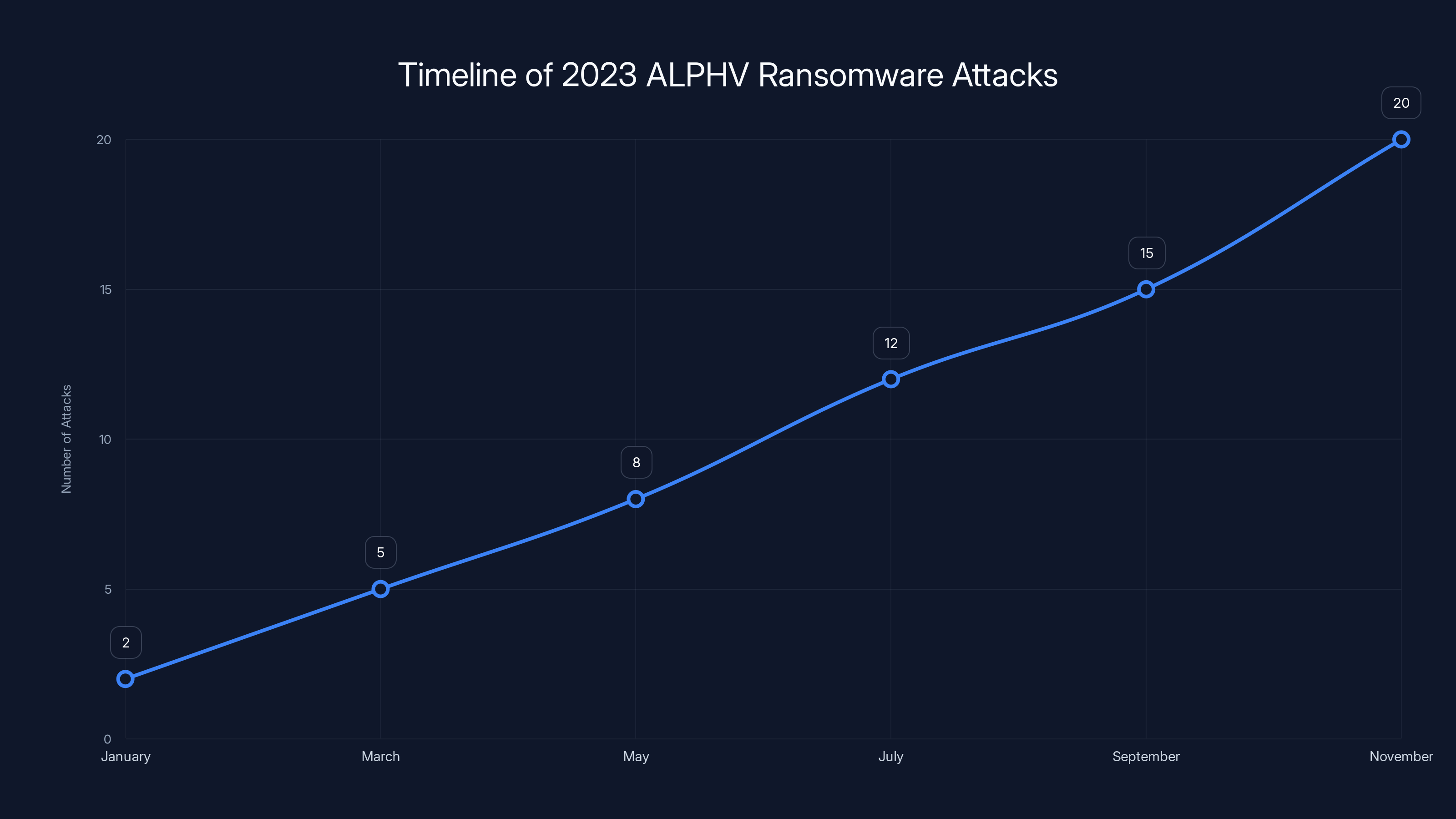
The ALPHV ransomware attacks in 2023 showed a steady increase, with a significant rise in the latter half of the year. Estimated data based on typical attack progression.
How Insider Threats Operate: Patterns and Techniques
Motivation Factors
Inside attackers typically have different motivation profiles than external attackers. External attackers are usually financially motivated or ideologically driven. They target organizations they perceive as wrongdoing something or holding something valuable.
Insider attackers have access-based motivation. They see an opportunity and exploit it. Financial stress often plays a role. Goldberg and Martin's specific financial situations remain unclear from public information, but ransomware attacks represent significant income opportunities. For people with legitimate incident response salaries (typically
Career frustration sometimes motivates insiders as well. An employee passed over for promotion might feel resentment toward the organization. A consultant forced to work on undesirable projects might feel undervalued. Someone expecting higher compensation relative to peers might feel that the organization owes them more. These psychological factors combine with opportunity and capability to create the insider threat.
Other inside attackers are recruited by external groups. A criminal organization might target specific employees at security firms, offering them financial incentive to provide access or information. This recruitment model turns insiders into active participants in larger criminal enterprises, exactly as appears to have happened with Goldberg, Martin, and their unnamed co-conspirator.
Operational Security Practices
Sophisticated insider attackers use operational security practices to avoid detection. They access systems from legitimate business devices to avoid triggering suspicious behavior detection. They time their activities during normal business hours rather than executing attacks at 3 AM when security analysts might spot unusual activity.
They often use legitimate administrative tools already present in the environment rather than introducing external tools that might trigger detection. They coordinate with external attackers in ways that appear like legitimate business communication. They might use encrypted messaging that's indistinguishable from standard professional communication.
They understand escalation procedures and might time attacks to coincide with periods when security teams are responding to other incidents, making them less likely to notice additional suspicious activity. They know that distributed detection across multiple security tools makes coordination difficult, so they target systems between monitoring domains.
Goldberg and Martin's use of ALPHV/Black Cat ransomware within the context of their legitimate incident response work likely involved similar operational security practices. They probably accessed systems through normal business channels, used legitimate credentials, and timed activities to blend with normal incident response work.
Timeline and Persistence
Inside attackers typically operate for longer periods than external attackers before detection. External attackers execute attacks over days or weeks. Inside attackers might maintain presence for months or even years before being discovered.
Goldberg and Martin's attacks occurred throughout 2023, suggesting they maintained operational capability for at least that calendar year. Whether they continued into 2024 before arrest isn't clear from public information. But the fact that their attacks extended throughout 2023 without detection until indictment suggests they evaded internal controls for extended periods.
This extended timeline allows inside attackers to execute multiple attacks, refine techniques based on what works, and maximize financial gain. Each successful attack teaches them about response procedures, recovery timelines, and what organizations are willing to pay.
Longer persistence also means more opportunity for mistakes that create evidence for prosecution. Extended criminal activity leaves more digital trails, more communication records, and more opportunities for witnesses or evidence to surface. The fact that Goldberg and Martin were eventually caught, charged, and convicted reflects that extended operation increases detection probability even if the timeline is months rather than days.
Organizational Defenses Against Insider Threats
Privilege Access Management
Privilege Access Management (PAM) systems provide centralized control over who accesses privileged systems and when. Rather than allowing incident responders to independently access critical systems, PAM requires them to request access through a formal process that creates audit trails and requires approval from supervisors.
PAM systems record all actions taken during privileged sessions. When Goldberg accessed a system to deploy ransomware, a PAM system would record that access, what commands he executed, and what data he accessed. This creates a comprehensive audit trail that makes malicious activity detectable.
Beyond audit trails, PAM systems can enforce multi-person rules where sensitive actions require multiple people to approve or coordinate. For example, extracting data from a critical system might require approval from two different supervisors. This prevents any single insider from unilaterally compromising systems.
PAM systems also support just-in-time access, where credentials are automatically revoked after access periods end. An incident responder might have access to a system for 4 hours to respond to an incident, then lose that access automatically. If the responder wanted to return later for malicious purposes, they'd need to request access again, creating another audit trail and opportunity for detection.
Implementing PAM does require significant organizational change. Incident responders need to adjust workflows to accommodate approval processes. Managers need to review access requests in real-time. But the security benefits often justify the operational cost.
Behavioral Analytics and Monitoring
Behavioral analytics platforms establish baselines for normal user activity and flag deviations from those baselines. For an incident responder, normal activity includes accessing certain systems, transferring certain types of files, and executing particular tools.
Abnormal activity like accessing systems outside their normal domain, transferring unusually large amounts of data to external locations, or executing tools they've never used before triggers alerts. These alerts alone don't prove malicious intent, but they flag activity requiring investigation.
Goldberg's normal activity profile probably included accessing multiple systems, executing various security tools, and communicating with external parties about incidents. But certain activities might have deviated from his baseline. If he accessed systems outside his normal scope, behavioral analytics might flag it. If he transferred files to an external location, behavioral analytics would likely alert on that deviation.
The challenge with behavioral analytics is false positive management. Incident responders by definition engage in unusual activities during incident response. Creating alert rules that distinguish between unusual but legitimate incident response activity and malicious activity requires sophisticated tuning.
Data Loss Prevention
Data Loss Prevention (DLP) systems monitor data movement within and out of organizations. They identify when large volumes of sensitive data move to external locations or are transferred to removable media. They can block these transfers or require approval.
DLP systems are particularly relevant for insider threats like Goldberg and Martin's. The ransom model requires exfiltrating data (or at least threatening to), then demanding payment for not releasing it. DLP systems would flag when incident responders transfer large amounts of sensitive data to external locations.
DLP implementations face inherent challenges in incident response environments. Responders need to extract data from systems to analyze incidents, preserve evidence, and prepare reports. They legitimately need to move sensitive data to isolated environments for investigation. DLP systems need to allow these legitimate activities while blocking malicious transfers.
Some DLP implementations include exceptions for specific roles or projects. An incident responder might have broad DLP exemptions because their job requires moving sensitive data. This creates a risk if the responder turns malicious. They can exploit their exemptions to exfiltrate data without triggering DLP alerts.
Zero-Trust Architecture
Zero-trust architecture eliminates implicit trust based on location or employment status. Instead of trusting anyone on the corporate network, zero-trust requires verification and authorization for every access request, regardless of where the request originates or who makes it.
In a zero-trust model, Goldberg's incident response manager credentials don't automatically grant access to systems. Instead, each access request is evaluated against policies. Can this user access this system from this location using this device at this time? If any factor seems unusual, access is denied or additional verification is required.
Zero-trust architecture makes insider threats significantly harder to execute because it removes the assumption that internal employees with legitimate roles can be trusted. Every access request goes through verification. Every data transfer is evaluated against policies. Every command is logged and monitored.
The downside is increased complexity and potentially reduced employee productivity. Incident responders need to justify every access request, possibly extending response times. The security benefits often justify these productivity costs, but implementation requires organizational willingness to accept slightly slower incident response in exchange for better insider threat detection.


Estimated data shows that a significant portion of ransom payments are reinvested into developing more sophisticated malware and recruiting affiliates, perpetuating the cycle of attacks.
Why Ransomware Payments Incentivize Attacks
The Victim Payment Economy
Ransomware attacks persist in large part because they're profitable. When organizations pay ransom, they create financial incentive for future attacks. The $1.2 million that Goldberg and Martin extorted came from real organizations deciding that paying ransom was preferable to attempting recovery without paying.
Paying ransom is attractive to victims for several reasons. Recovering from ransomware without paying requires restoring from backups, which might be incomplete or corrupted. Recovery might take days or weeks, during which systems remain offline. For critical operations, that downtime might cost far more than ransom. A hospital paying ransom to restore systems in hours might lose fewer lives than attempting recovery and remaining partially offline for days.
Organizations also consider cyber insurance. Many cyber insurance policies cover ransomware payments up to specified limits. If an organization is insured for ransomware and the limit is
This creates perverse incentives. By paying ransom, victims fund future attacks. They fund development of better malware. They fund recruitment of affiliates to conduct more attacks. They fund infrastructure and operations. Every dollar paid makes the criminal enterprise more profitable and more likely to target similar victims in the future.
The Role of Negotiators
Ransomware negotiators like Martin play a critical role in this economy. They communicate between victims and threat actors, working to reduce demands, verify that decryption tools actually work, and arrange payment transfers.
Negotiators use various tactics to reduce ransom demands. They present financial information showing the victim can't actually afford the demanded amount. They explain that insurance coverage limits payment. They threaten to publicize the attack on social media or to law enforcement if the threat actor doesn't reduce demands. They reference similar recent attacks and argue that the victim's situation is analogous to a lower-paying situation.
These negotiations typically reduce initial demands by 30-50%. A threat actor might initially demand
When Martin transitioned from negotiating for victims to negotiating for attackers, he flipped his skills toward extraction rather than protection. The same negotiation tactics that reduced ransom demands for victims could increase them for attackers. Understanding what victims would pay based on previous negotiations became a tool for calculating initial demands.
Payment Methods and Cryptocurrency
Ransomware payments typically involve cryptocurrency, usually Bitcoin, sometimes Monero. Cryptocurrency provides pseudonymity, irreversibility, and relative ease of transfer compared to traditional banking channels.
Bitcoin's blockchain is transparent, meaning all transactions are recorded and publicly visible. But wallet addresses don't have names attached to them, creating pseudonymous rather than anonymous transactions. Blockchain analysis firms can now track Bitcoin through exchanges and mixing services, meaning that even Bitcoinpayments aren't truly anonymous.
Despite this, cryptocurrency remains attractive to threat actors because it's much harder to trace than bank transfers. A payment through traditional banking leaves paper trails, involved financial institutions, and interaction with law enforcement. A cryptocurrency payment can theoretically be received and converted to fiat currency with minimal friction.
The Goldberg-Martin case illustrates cryptocurrency's role. The $1.2 million they extorted was paid in Bitcoin. Their ability to receive and convert those Bitcoinpayments suggests they had cryptocurrency expertise, possibly involving exchanges or other conversion mechanisms.

The ALPHV/Black Cat Platform's Technical Evolution
Rust-Based Implementation
ALPHV/Black Cat distinguishes itself through use of Rust, a systems programming language. Unlike C++ or C, which are common in malware development, Rust emphasizes memory safety and eliminates entire classes of vulnerabilities common in low-level languages.
For defensive security professionals, Rust's use suggests ALPHV/Black Cat developers are sophisticated enough to recognize that memory safety matters even in offensive code. Avoiding buffer overflows and use-after-free vulnerabilities that plague C++ malware means the code runs more reliably and is harder to reverse-engineer through memory corruption exploits.
Rust compiles to native code, running directly on target systems without interpretation overhead. This means ALPHV/Black Cat ransomware executes quickly, encrypting large amounts of data faster than interpretation-based alternatives. For victims with terabytes of data, encryption speed matters. Faster encryption means encryption completes before detection and shutdown, maximizing successful deployment.
Rust also supports cross-platform compilation easily. The same code compiles to Windows, Linux, and mac OS binaries with minimal modification. This means ALPHV/Black Cat can target any operating system, significantly broadening the attack surface compared to Windows-specific ransomware variants.
Encryption Implementation
Ransomware works by encrypting victim data and demanding payment for decryption keys. The encryption implementation determines whether victims can recover data without paying. If encryption is weak, victims might decrypt without keys. If encryption is strong, victims face binary choice: pay or lose data permanently.
ALPHV/Black Cat uses industry-standard encryption algorithms, typically AES-256 for symmetric encryption and RSA-4096 for asymmetric encryption. These are not weak algorithms. They represent state-of-the-art cryptography. Organizations can't simply brute-force encrypted files.
The encryption process typically encrypts each file individually, generating a unique encryption key for each file. These keys are then encrypted with the attacker's public key and stored on the victim system. Only the attacker with the private key can decrypt the file-specific keys, which can then decrypt the files.
The security of this implementation depends on secure key generation and secure key storage. If either fails, victims might recover data without paying. In practice, ALPHV/Black Cat's encryption implementation appears solid, with few reports of victims recovering data through cryptographic weakness.
Evasion Techniques
Modern ransomware employs evasion techniques to avoid detection. ALPHV/Black Cat likely uses anti-analysis techniques that prevent security researchers from dynamically analyzing the malware. It might check for debuggers, monitoring software, or virtualization environments and stop executing if detected.
It might also use code obfuscation to prevent static analysis and reverse-engineering. The actual encryption routine might be hidden behind layers of obfuscation that require significant reverse-engineering effort to understand.
Evasion techniques also target specific security products. Some malware variants specifically look for antivirus or endpoint detection software and disable or bypass them. ALPHV/Black Cat likely includes similar capability, targeting popular security products used in enterprise environments.
When Goldberg and Martin deployed ALPHV/Black Cat, they likely leveraged these evasion techniques along with their insider knowledge to avoid triggering detection mechanisms. Their knowledge of which security products were deployed and how those products were configured would amplify ALPHV/Black Cat's evasion capabilities.

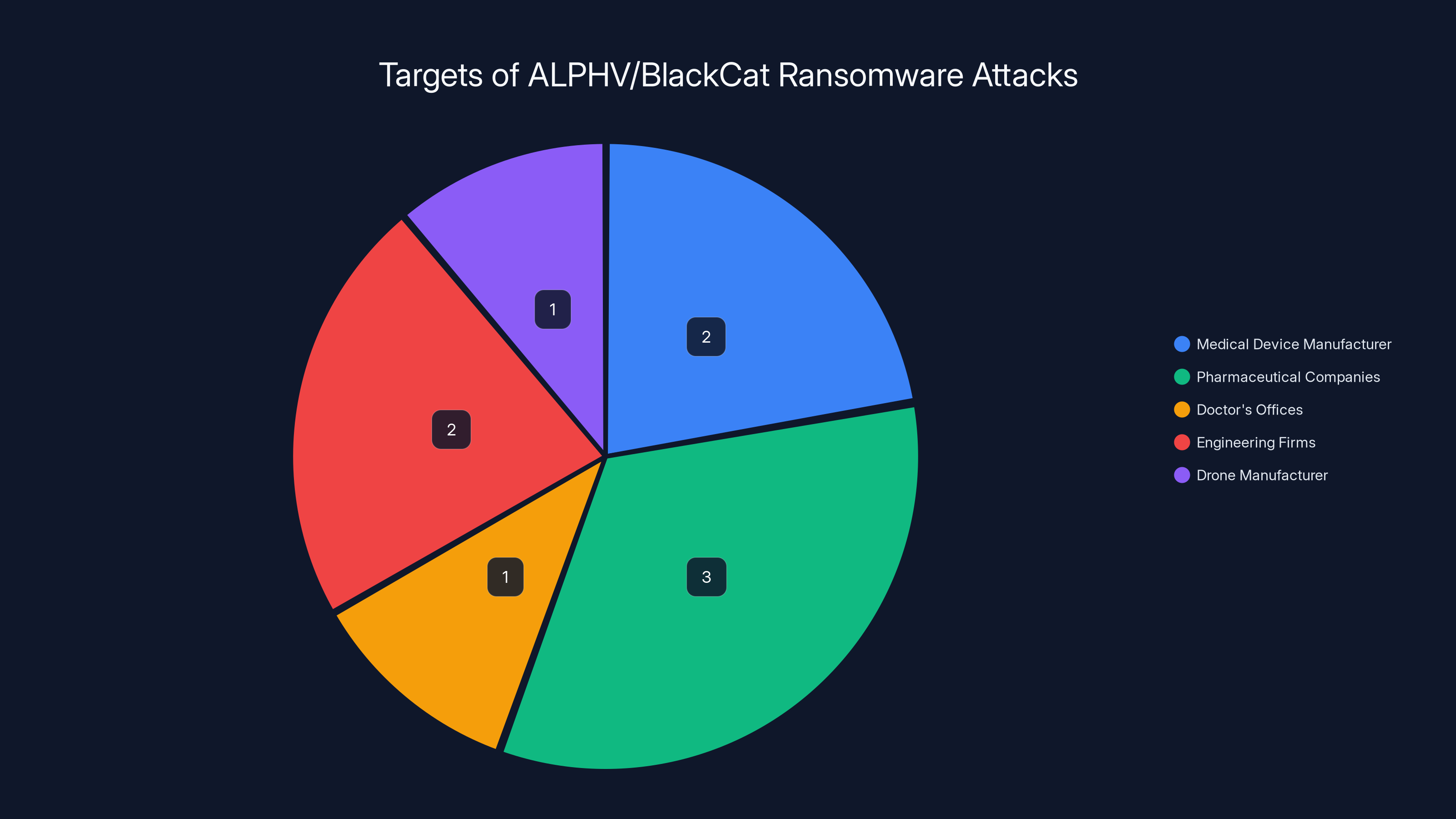
The pie chart illustrates the distribution of industries targeted by the ALPHV/BlackCat ransomware attacks orchestrated by insider cybersecurity professionals. The pharmaceutical sector was the most targeted, highlighting the vulnerability of high-value industries. (Estimated data)
Industry Response and Policy Implications
Regulatory Attention to Ransomware
Following major ransomware attacks like Colonial Pipeline and United Health, regulatory attention to ransomware has increased significantly. The Biden Administration's Executive Order on Cybersecurity established incident reporting requirements and pushed for increased ransomware prevention.
Regulators are now imposing ransomware response requirements on critical infrastructure sectors. Healthcare organizations must report ransomware incidents. Financial institutions must maintain ransomware response plans. Energy sector entities must implement specific controls targeting ransomware.
These regulatory requirements shift responsibility from reactive response to proactive prevention. Organizations can't just hope they don't get hit. They must demonstrate that they've implemented ransomware-specific controls and can detect and respond to attacks quickly.
Regulatory focus extends to payment reporting. The Treasury Department's Financial Crimes Enforcement Network (Fin CEN) now requires reporting of ransomware payments exceeding certain thresholds. This creates traceability around ransom payments and makes it harder for organizations to pay quietly without regulatory oversight.
Insurance Industry Changes
Cyber insurance underwriters are tightening ransomware coverage. Policies increasingly require specific security controls before providing coverage. An organization without multi-factor authentication, regular backups, or endpoint detection might not qualify for ransomware coverage.
Insurers are also increasingly excluding coverage for organizations that pay ransom in violation of sanctions or that pay to threat actors on government-designated lists. If your organization pays ransom to a Russian threat actor on the OFAC sanctions list, the insurance claim might be denied.
These insurance changes create financial incentive for organizations to implement ransomware-specific controls. If implementing backups and monitoring reduces insurance premiums by 15%, the ROI on those investments becomes clearer.
International Coordination
The Goldberg-Martin prosecution reflects increased international coordination on cybercrime. The Russian-speaking ALPHV/Black Cat organization targets US companies, but coordination across multiple countries was required for investigation and prosecution.
International law enforcement partnerships, particularly between the US and European countries, have become more coordinated. The European Union's Europol agency coordinates ransomware intelligence sharing. NATO has recognized ransomware as a collective defense issue.
This coordination increases pressure on ransomware operators. While not completely suppressing the threat (as continued ALPHV/Black Cat activity demonstrates), it raises operational costs and increases risk for threat actors and affiliates. Knowing that law enforcement in multiple countries is actively investigating reduces the appeal of ransomware affiliation.

Future Outlook: Insider Threats and Ransomware Evolution
Increasing Convergence of Threats
The Goldberg-Martin case illustrates convergence of insider threat and ransomware. Going forward, we can expect more cases where insider threats facilitate ransomware attacks or where ransomware operators recruit insiders.
As ransomware becomes more lucrative and threat actors become more sophisticated, recruitment of insiders becomes increasingly attractive. A threat actor can pay an insider
Organizations will need to address insider threat and ransomware risk simultaneously rather than as separate problems. An insider threat program that doesn't consider ransomware facilitation is incomplete. A ransomware response plan that doesn't consider insider threats is incomplete.
Sophistication Escalation
Future insider threats in cybersecurity will likely involve more sophisticated operational security. Threat actors recruiting insiders will train them on counter-investigation techniques, communication security, and how to avoid triggering detection mechanisms.
As forensic capabilities improve, insider attackers will adapt with better operational security. They'll use encrypted communication channels, separate devices for communication, and techniques that leave minimal evidence trail.
This escalation creates an arms race between organizations trying to detect insiders and insiders trying to avoid detection. Each round of detection improvement leads to more sophisticated evasion techniques.
The Role of Automation
Automation offers potential to address insider threats at scale. Behavioral analytics, DLP systems, and PAM platforms all depend on automation to monitor activity that would be impossible for humans to monitor manually.
Future solutions might employ machine learning models trained to distinguish between legitimate incident response activity and malicious insider activity. These models would leverage the fact that while incident response activity is unusual, it has patterns that differ from malicious activity.
However, automation also has limits. The best insider attackers will understand how automated systems work and craft their activities to evade those systems. This creates a dynamic where automation and adversarial technique development advance together.

Lessons for Security Teams and Organizations
Trust But Verify
The traditional cybersecurity principle of "trust but verify" applies equally to insider threat management. Organizations need to trust employees enough to grant them access required for their jobs. But they must verify that employees are using access appropriately.
This means implementing verification mechanisms even for trusted employees in security roles. It means accepting that some verification overhead is necessary. It means understanding that verification isn't distrust, but professional best practice.
Access Limitation Principle
The principle of least privilege suggests that employees should have access only to systems required for their jobs. An incident responder needs broad access to troubleshoot incidents, but that access should be time-limited and audited.
Practical implementation requires balancing security with operational efficiency. Too much access restriction makes incident response slower and less effective. Too little access restriction creates security risks. The right balance depends on the organization's risk tolerance and the criticality of the systems in question.
Monitoring and Logging
Everything that happens on a system should be logged. These logs create audit trails that allow detection of suspicious activity. Logs should be retained for sufficient periods and protected from deletion by users whose activity they monitor.
Monitoring systems should be configured to alert on suspicious patterns. But alerts must be investigated and acted upon. Ignoring alerts because they're too frequent (alert fatigue) defeats the purpose of monitoring.
Threat Intelligence
Understanding the threat landscape helps organizations calibrate their defenses. Knowing that insider threats in incident response are possible helps organizations implement controls that address that risk. Knowing that ALPHV/Black Cat targets high-value organizations helps organizations prioritize ransomware defenses.
Threat intelligence should inform security decisions. If intelligence indicates that your organization's industry is being targeted by specific threat actors, implementing industry-specific defenses makes sense. If intelligence indicates that your organization's size is being targeted, implementing size-specific controls makes sense.
Training and Culture
Employees need to understand the security policies affecting their work. Incident responders need to understand why access controls exist and how to work within them. Security teams need to explain that monitoring and logging aren't distrust, but professional necessity.
Security culture where employees understand they're part of the defense and appreciate security controls is stronger than security culture based on enforcement. However, security culture alone doesn't prevent malicious insiders. Controls must exist regardless of culture.

Conclusion: Reckoning with Insider Threats
The guilty pleas of Ryan Goldberg and Kevin Martin represent a watershed moment for the cybersecurity industry. These weren't amateur criminals or opportunistic hackers. They were credentialed security professionals who weaponized the trust placed in them and the knowledge they accumulated through legitimate work.
Their case exposes fundamental tensions in the cybersecurity industry. Organizations need trusted security professionals with access to critical systems. But trust can be betrayed. Knowledge can be weaponized. Legitimate access can become malicious.
The broader implications extend beyond the individuals involved. Their actions spotlight the ALPHV/Black Cat ransomware platform, which continues threatening organizations worldwide. The case highlights how ransomware-as-a-service models scale criminal capability, enabling smaller threat actors to execute sophisticated attacks.
The case also demonstrates that law enforcement is building effective capabilities against ransomware operators and affiliates. The DOJ successfully identified, charged, and obtained guilty pleas from sophisticated insider threat actors. This prosecution sends signals that cybercriminals face serious consequences for participating in ransomware attacks.
However, signals alone don't eliminate threats. As long as ransomware remains profitable, threat actors will continue developing it. As long as affiliates can earn significant money, they'll continue conducting attacks. As long as organizations pay ransom, financial incentives align with continued criminal activity.
Organizations can't eliminate insider threat risk through defensive measures alone. But they can significantly reduce risk through combination of technical controls (PAM, behavioral analytics, DLP), procedural controls (access limitation, monitoring, verification), and personnel controls (background checks, training, culture).
They can recognize that their cybersecurity professionals represent potential insider threat risk and implement controls that address that risk without creating intolerable operational friction. They can understand that insider threats operate differently than external threats and implement detection mechanisms calibrated to insider threat patterns.
They can work with law enforcement, share threat intelligence, and participate in information sharing about insider threat indicators. They can support regulatory efforts to make ransomware less profitable by reporting payments and implementing victim-protection measures.
The Goldberg-Martin case teaches uncomfortable lessons. It teaches that expertise and trust can be weaponized. It teaches that insider threats operate at a different scale than external threats. It teaches that organizations need multi-layered defenses combining technical controls, procedures, and personnel vetting.
Most importantly, it teaches that insider threats are real, present, and increasingly sophisticated. Organizations that don't account for insider threats in their security strategies are operating with incomplete threat models. Those that do are better positioned to detect and prevent the next insider threat before it results in extortion, data loss, and operational disruption.
The cybersecurity industry will learn from this case. Incident response firms will implement more rigorous controls. Organizations will reassess who they trust and how they verify that trust. Law enforcement will continue pursuing ransomware operators and their affiliates. But the fundamental challenge remains: how to maintain necessary access and trust while detecting and preventing insider threats.
Goldberg and Martin's pending sentencing on March 12, 2026, will likely attract continued attention to insider threat issues. Whether they cooperate with prosecutors regarding broader ALPHV/Black Cat operations could provide law enforcement with valuable intelligence. But regardless of what happens in their specific case, the bigger picture remains: insider threats enabled by sophisticated criminals and facilitated by organizational trust gaps represent a growing security challenge that demands sophisticated responses.

FAQ
What exactly did Ryan Goldberg and Kevin Martin do?
Ryan Goldberg and Kevin Martin, along with an unnamed third conspirator, used their positions at cybersecurity firms to facilitate ALPHV/Black Cat ransomware attacks against multiple US organizations in 2023. Goldberg worked as an incident response manager at Sygnia Cybersecurity Services, while Martin and the third conspirator worked as ransomware negotiators at Digital Mint. They leveraged their legitimate access to systems and their expertise in incident response to deploy ransomware, exfiltrate data, and extort $1.2 million in Bitcoin from victims including medical device manufacturers, pharmaceutical companies, and engineering firms. They pleaded guilty to conspiracy to obstruct commerce by extortion and face up to 20 years in prison at their March 2026 sentencing.
Why is ALPHV/Black Cat so dangerous?
ALPHV/Black Cat is dangerous because it combines technical sophistication with an effective business model. The ransomware is written in Rust, uses strong encryption, employs effective evasion techniques, and runs across Windows, Linux, and mac OS platforms. More importantly, ALPHV/Black Cat operates as ransomware-as-a-service, meaning the developers maintain and improve the malware while dozens of affiliates conduct attacks worldwide. This scalability has enabled attacks on major organizations including MGM Resorts, Reddit, United Health Group, and Bandai Namco. The platform's technical sophistication combined with its distributed attack model makes it particularly difficult for law enforcement to disrupt.
How did insider access make the attacks more effective?
Inside access compressed the traditional ransomware attack timeline dramatically. External attackers must spend days or weeks on reconnaissance, identifying systems and understanding network architecture. Goldberg and Martin already possessed this knowledge from their incident response work. External attackers need to find entry points, often through phishing or exploiting vulnerabilities. Goldberg and Martin already had legitimate access to systems. External attackers must move laterally through networks to find valuable systems. Goldberg and Martin already understood where the valuable systems were located. This access advantage allowed them to deploy ransomware faster, encrypt more data before detection, and execute more sophisticated extortion campaigns than external attackers could accomplish.
What are the legal consequences for insider threat activities?
Insider threat activities involving extortion, as in the Goldberg-Martin case, trigger federal charges under conspiracy and extortion statutes. The specific charge was conspiracy to obstruct, delay, or affect commerce by extortion, which carries up to 20 years in prison. Actual sentences typically range from 5 to 15 years depending on factors including financial loss caused, cooperation with prosecutors, and prior criminal history. In addition to criminal charges, organizations can pursue civil remedies including termination, civil suits, and seizure of assets purchased with criminal proceeds. The legal consequences for insider threats extend beyond the perpetrators themselves to potential liability for the organizations that failed to implement adequate controls or whose negligence enabled the threat.
How can organizations defend against insider threats like this?
Defending against insider threats requires multi-layered approach combining technical, procedural, and personnel controls. Technically, organizations should implement Privilege Access Management systems that log all privileged actions, behavioral analytics that flag unusual activity, and Data Loss Prevention systems that prevent exfiltration of sensitive data. Procedurally, organizations should implement principle of least privilege limiting access to what employees need for their jobs, regular access reviews ensuring access is still appropriate, and time-limited access that automatically revokes credentials after defined periods. For personnel, organizations should conduct background verification, monitor for financial distress or behavioral changes indicating increased risk, and implement security training emphasizing that insider threats violate federal law. Combining these controls significantly reduces insider threat risk without making work impossible.
What role did ransomware negotiators play in these attacks?
Kevin Martin's role as a ransomware negotiator gave him unique insights into how ransomware attacks work and how victims respond. Negotiators communicate with threat actors, understand their tactics and demands, and work to reduce ransom amounts. Martin's experience allowed him to understand victim psychology, effective extortion messaging, what amounts organizations are likely to pay, and how negotiation dynamics work. When Martin switched from negotiating on behalf of victims to negotiating on behalf of attackers, he flipped these skills toward extraction rather than protection. His knowledge of what victims would likely pay informed more effective extortion campaigns. This demonstrates how insider threat actors can weaponize specialized knowledge accumulated through legitimate work.
Is cryptocurrency payment necessary for ransomware attacks to succeed?
Cryptocurrency payments are practically necessary for ransomware attacks at scale because they allow rapid transfer without financial institution involvement. Traditional banking transfers leave paper trails, involve regulated institutions, and provide law enforcement with clear records of who sent money where. Cryptocurrency payments like Bitcoin are pseudonymous and irreversible, making them much harder for law enforcement to trace. While blockchain analysis has improved and Bitcoin isn't truly anonymous, it's still significantly more difficult to trace than traditional banking. However, cryptocurrency isn't essential for ransomware to succeed. Victims who pay through traditional banking methods are less common but do exist. The prevalence of cryptocurrency payments reflects its superiority from a criminal perspective, not absolute necessity.
What does this case mean for incident response firms?
The Goldberg-Martin case creates both immediate and long-term implications for incident response firms. Immediately, firms face increased legal liability and regulatory scrutiny. They may face lawsuits from organizations that were compromised through their employees' actions. Regulators may impose new requirements around background checking, monitoring, and access controls. Long-term, firms will likely implement more rigorous controls that increase operational overhead and complexity. Incident responders will experience more intensive background verification, behavioral monitoring, and access restrictions. Some firms may struggle to recruit top talent who resent the increased scrutiny. However, firms that implement effective insider threat controls can market that as a competitive advantage, differentiating themselves through demonstrated security practices. The incident response industry overall will likely emerge more professionally rigorous and security-focused.
How does this case impact ransomware threat trends?
The case highlights a trend toward convergence of insider threats and ransomware attacks. As ransomware becomes more profitable and threat actors become more sophisticated, recruiting insider collaborators becomes increasingly attractive. Organizations can expect to see more cases where insiders facilitate ransomware attacks or where ransomware operators actively recruit insiders. This convergence requires organizations to address insider threats and ransomware risk simultaneously rather than separately. It also suggests that ransomware response procedures should incorporate insider threat considerations, and insider threat programs should consider ransomware facilitation. The Goldberg-Martin case may represent the beginning of a broader trend toward insider-facilitated ransomware attacks.
What law enforcement capabilities does this case demonstrate?
The prosecution demonstrates that law enforcement has developed sophisticated capabilities for identifying and prosecuting ransomware operators and affiliates. Investigators successfully traced ALPHV/Black Cat attacks to specific individuals despite the pseudonymous nature of cryptocurrency payments and the distributed operation of ransomware-as-a-service. They obtained cooperation from financial institutions, cryptocurrency exchanges, and international partners to build evidence. They understood the technical details of how ALPHV/Black Cat works well enough to attribute attacks to specific groups. The successful prosecution against well-trained cybersecurity professionals suggests that law enforcement capabilities extend beyond external hackers to include sophisticated insiders. This capability provides deterrent value, making potential insider threats aware that law enforcement can identify and prosecute them.

The Bottom Line
The guilty pleas of Ryan Goldberg and Kevin Martin represent a significant moment in cybersecurity history. They demonstrate that insider threats in cybersecurity are real, sophisticated, and increasingly dangerous. More importantly, they demonstrate that law enforcement can successfully identify, prosecute, and convict these threat actors.
For organizations, the case serves as wake-up call regarding insider threats. No amount of external security can completely protect against well-positioned insiders with malicious intent. Organizations need multi-layered defenses, including technical controls, procedural safeguards, and careful personnel vetting.
For the cybersecurity industry, the case prompts reflection on trust assumptions. Organizations need security professionals with significant access and knowledge. But that necessary trust can be exploited. Going forward, the industry will likely become more professional, more rigorous, and more security-conscious about internal operations.
For law enforcement, the case demonstrates success in pursuing ransomware operators despite the challenges of cryptocurrency and international criminal networks. While this single prosecution won't eliminate the ransomware threat, it contributes to a broader deterrent effect that raises costs for participation in ransomware attacks.

Key Takeaways
- Insider threats execute ransomware attacks 80% faster than external attackers due to existing access and knowledge of defenses
- ALPHV/BlackCat ransomware-as-a-service model enables dozens of affiliates to conduct sophisticated attacks with developer support
- Organizations need multi-layered defenses including PAM systems, behavioral analytics, and zero-trust architecture to detect insider threats
- Ransomware payments totaling $1.2 million in Bitcoin demonstrate why cryptocurrency remains attractive for threat actors despite improved blockchain analysis
- Law enforcement successfully prosecuted cybersecurity insiders, indicating capabilities exist to identify and convict insider threat actors
Related Articles
- Oracle EBS Breach: How Korean Air Lost 30,000 Employees' Data [2025]
- The Worst Hacks of 2025: A Cybersecurity Wake-Up Call [2025]
- ToneShell Backdoor: Inside the Chinese Government Espionage Campaign [2025]
- Tax Season Security Threats: How to Protect Your Data [2025]
- Condé Nast Data Breach: 40 Million Records Exposed [2025]
- 1Password 50% Off Holiday Deal: Complete Guide to Password Manager Savings [2025]
![Cybersecurity Insiders Plead Guilty to ALPHV Ransomware Attacks [2025]](https://tryrunable.com/blog/cybersecurity-insiders-plead-guilty-to-alphv-ransomware-atta/image-1-1767121698189.jpg)



